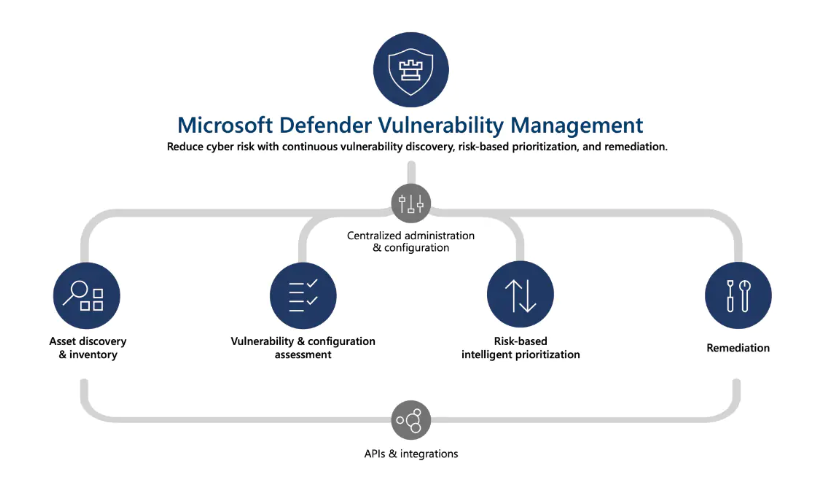
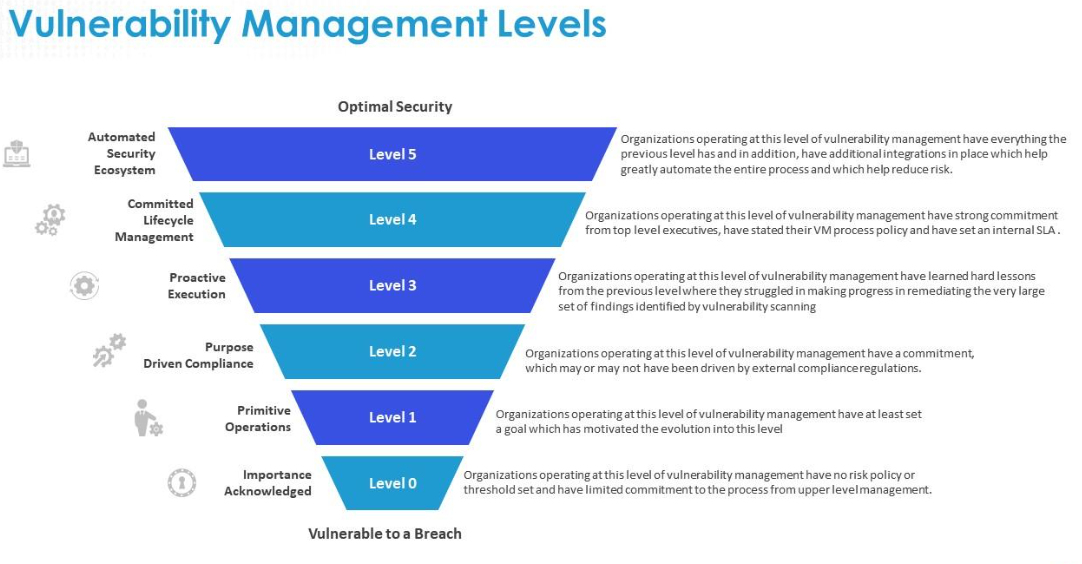
The concept of enterprise vulnerability management comes from the fact that every online data needs to be arranged sequentially and should be maintained properly so that there doesn’t exist any security threat to it. All the networks and connections that are attached to the vulnerability network can be tracked down properly and if any suspicious account or network is found, then it can be blocked or deleted well in time.
Ways to facilitate yourself with Enterprise Vulnerability Management –
Following are some important and impactful ways to facilitate yourself with enterprise vulnerability through it managed services provider providers very appropriately:
-
AutomCation of Leverages is done appropriately –
Leverages should be kept automated so that any kind of changes to be made are done automatically.
-
Threat Intelligence never Disappoints people –
Threat Intelligence is a concept of threat detection that needs to be implemented on your network so that any kind of future troubles are avoided.
-
Categorize the Vulnerabilities according to your Requirements –
Another important way of facilitating yourself with the best enterprise vulnerability systems is to categorize all the available vulnerabilities properly. This categorization or sorting will help you build a strong network and eliminate all possible threats from the same.
By considering all the above ways to facilitate yourself with enterprise management through authentic IT managed services provider providers, you can get great help regarding your IT services and proper regulation of your technical works can be done. Enterprise vulnerability will help you make sure that no intruder damages your top-secret information and misuse it against you in whichever possible manner.
Conclusion
The process of enterprise vulnerability assessment is done in various steps which include identifying, prioritizing, sorting, and defining all the eligible vulnerabilities. Then the elimination of the inappropriate ones is done from the networks and the ones that are credible enough to provide benefits to the software are chosen. This whole process is carried out in steps and takes some time to get completed so that the results are completely up to the mark and uncompromised.
Hence, the right enterprise vulnerability management system needs to be by your side always so that you can be relaxed about the networks that your system is coming in contact with and the harm caused by them. However, all this is possible only when you choose the right management system to be by your side and not any random one.